Any IAM identity starts with no permissions, with the exception of account root user.
- Global, globally resilient
- Free
- Allow or Deny its identities on its AWS account
- Has no direct control on external accounts or users
- Identity federation and MFA
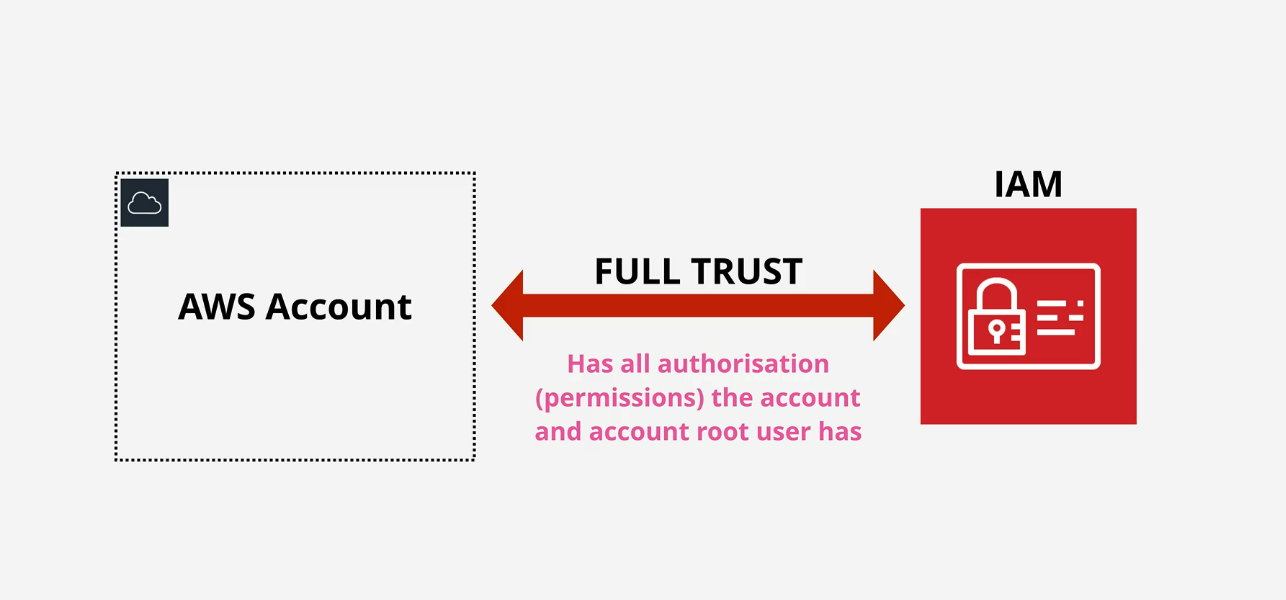
Each account has its own instance of IAM (something like a “database”). IAM is trusted fully by the account. It has all authorization (permissions) the account and account root user has.
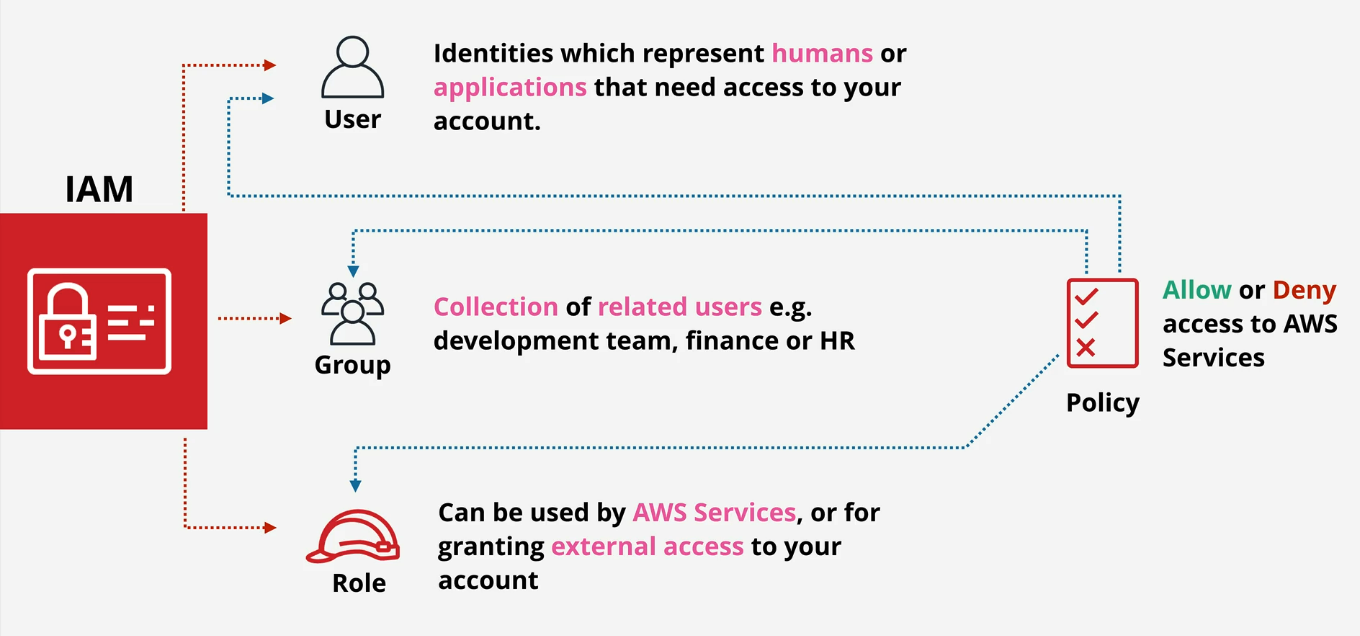
There are 3 different types of identity objects:
Policies can be attached to the listed identity objects.
Main jobs:
- It’s an identity provider (IDP): create and delete users, manage roles etc.
- It authenticate these identities.
- It authorize these identities to access (allow or deny) AWS resources.
